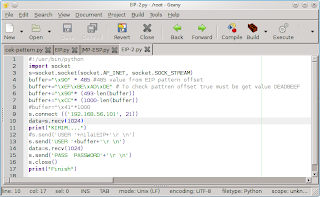
1. Create fuzzer with python.
2. Running Bigant on windows xp.
3. Running fuzer ==> # python fuzzer.py
4. To see effect of fuzzer open ollydb
5. View--SEH chain and shift+F9
6. Search running library service (.dll ) to jump POP POP RETN
==> In this case use vbajet32.dll
7. Copy vbajet32.dll to backtrack and cek dllcharacteristic with msfpescan.
8. Open module vbajet32.dll ==> Executables Modules==>search for
==> Sequence of command
9. Search POP POP RETN to see address.
10. Now look for address which use for control CPU.
11. Looking for offset==> using create pattern with Msf==>Fuzzer
12. Running fuzzer and see the result.
13. View==> SEH chain to see seh result
14. Shift + F9==> to see value in EIP==> cek offset value with pattern offset
15. Cek bad charackter ==> if seh chain to vbajet32.dll ( it's sound good).
==> I will explain to observation bad char in next section
Assumed we know the bad char is 0x00 0x0a 0x0d 0x20 0x25
16. Generate payload with msfweb
17. Modify Fuzzer with payload content.
18. Execute Fuzzer & telnet
==> DONE <==
===================================================================================
===================================================================================